Editor’s Note – It has come to the attention of DHS and the FBI that two separate consumer and business water systems have come under attack by hackers on the payroll of Russia. Both agencies are not releasing any formal alert on these events as no one knows exactly what happened or how to handle it, but be sure, there was hacking going on. This cyber assault was either by a virus or a worm in the software or of the telecom connectivity to SCADA. The result is pumping systems are failing and we deserve to know the real condition and threat. SUA has posted so much about Cyber-threats that is actually getting tiresome, but it is tantamount to understand who the hackers are, what they are doing, who is paying them, what the end-game is, and where our government is on safety and protection.
Second water utility reportedly hit by hack attack
Proof-of-concept intrusion
By Dan Goodin
Images posted online suggest that hackers may have gained unauthorized access to computers controlling a second water treatment facility, a claim that raises additional concerns about of the security of the US’s critical infrastructure.
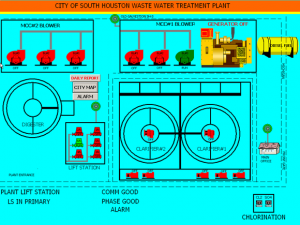
Five computer screenshots posted early Friday purport to show the user interface used to monitor and control equipment at the Water and Sewer Department for the City of South Houston, Texas. They were posted by someone calling himself pr0f to counter comments included in a Register article posted on Thursday in which a US Department of Homeland Security spokesman responded to reports of an attack on a separate water plant by saying there was no “credible corroborated data” indicating critical infrastructure was at risk.
Check out the vivid screen shots from the city of South Houston at these links:
“I dislike, immensely, how the DHS tend to downplay how absolutely FUCKED the state of national infrastructure is,” the post stated. “I’ve also seen various people doubt the possibility an attack like this could be done.”
pr0f went on to post what he claims is proof that internet-connected computers controlling other industrial equipment are easily accessible to unauthorized parties. The five pictures show what appears to be the HMI, or human machine interface, controlling highly sensitive equipment used by South Houston’s Water and Sewer personnel. One interface depicts an apparatus for monitoring and controlling the city’s waste-water treatment plant, including a power generator and what appear to be “blowers”, which control air flow.
The Register was unable to confirm claims that the images were obtained through the unauthorized access of the system. City officials have yet to confirm or deny pr0f’s claims, and representatives with DHS didn’t respond to an email seeking comment. The possibility that screen captures of the city’s industrial control systems were made by authorized employees for training or other purposes and later obtained by pr0f can’t be ruled out.
The posting comes a day after industrial control systems security expert Joe Weiss disclosed contents of a November 10 report from the Illinois Statewide Terrorism and Intelligence Center. It claimed that attackers destroyed a pump belonging to a regional water utility in that state by hackers who gained access to supervisory control and data acquisition systems that manage the utility’s machinery. That report remains unconfirmed, although the DHS spokesman said officials from his agency and the FBI are investigating.
While the events over the past two days have yet to be verified, there’s no denying that huge amounts of machinery used in gas refineries, power plants, and other industrial facilities are controlled by computers that are connected to the internet. This raises the specter of core parts of the nation’s infrastructure being taken over and sabotaged if hackers figure out ways to bypass their security controls. Officials are frequently aware of the risks, but financial constraints and personnel matters often trump those concerns.
“For folks with less resources available and tighter budgets, (there’s) web-based remote access,” said Michael Assante, a SCADA security expert and president of the National Board of Information Security Examiners, a nonprofit focused on security workforce training. Having controls available over the internet means many cash-strapped agencies don’t have to have dedicated SCADA engineers on premises around the clock, he explained. “They’re trying to use the technology to maximize the resources they have available to them.”